Synology NAS is the most versatile, easy to use, NAS system to date. You can replace expensive servers or even cloud services with a Synology NAS. If you are using in within the company, you can use it to store backups, replace an expensive backup appliance with a combination of NAS and Nakivo Backup & Replication, replace Windows file share, replace expensive NVR and in my case, replace Google Apps, Office Online with Synology Office. Once you connect AD with Synology, you can use existing users in Synology Office so the onboarding is dead simple.
But, since Synology NAS is also software-based, it is vulnerable to various exploits. In some cases there is malware targeting Synology devices, in some cases, Cryptolocker can infect files shared on the Synology NAS. But sometimes, Synology NAS can fall victim to bad security practice. For example, if the user that configured it, used bad security practice from the start, like using a commonly used password. In order to help you secure your Synology NAS, I created this tutorial. Should you follow it, you will minimize security issues to the minimum.
How to secure Synology NAS
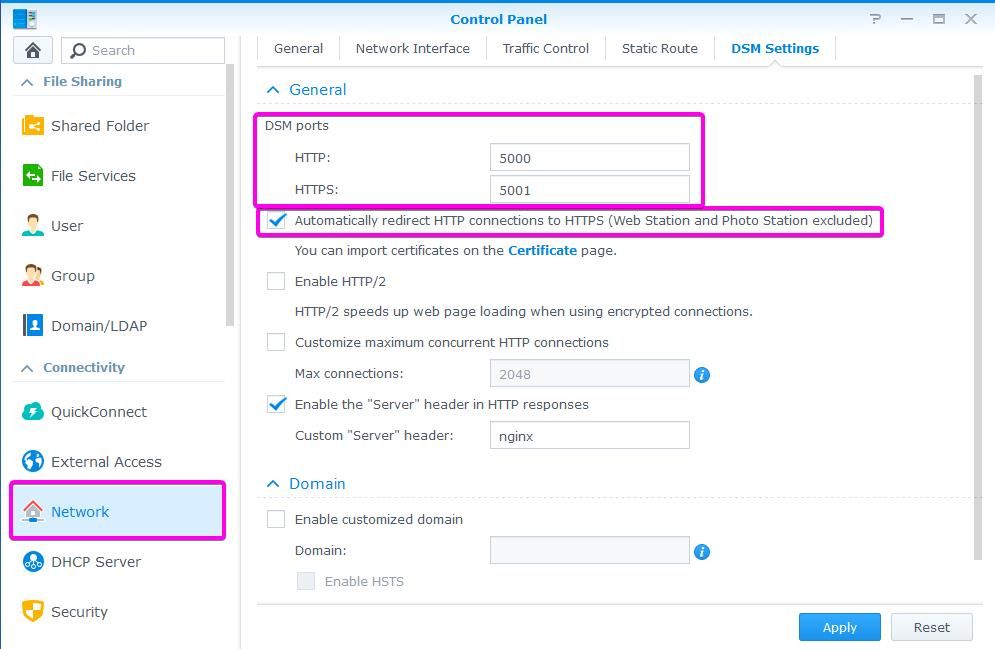
When you setup Synology NAS for the first time, it will start in HTTP mode. The best practice is to change DSM ports for HTTP and HTTPS access. You can use any number other than 5000 and 5001. The next step is to Automatically redirect HTTP connections to HTTPS. We need to that so that we prevent hackers from snooping for the passwords when we log in. When the traffic is HTTPS based communication is encrypted so it is not visible to prying eyes. You will find this setting if you open the Control panel, go to the Network and DSM settings.
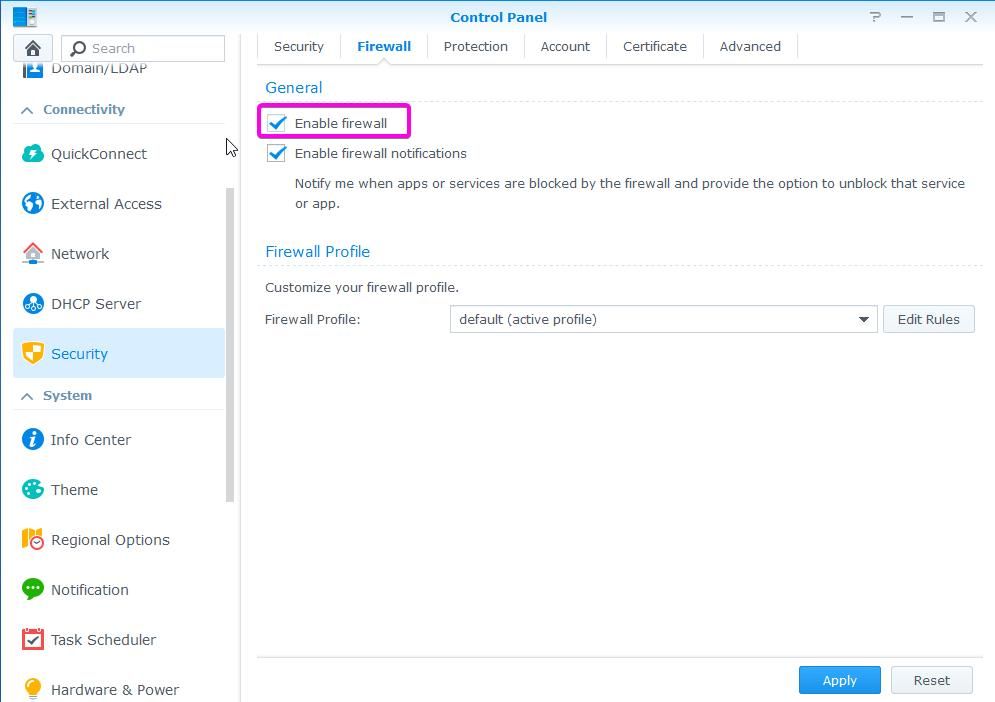
If you expose your NAS to the internet, it is advisable to enable the firewall so that you are protected from the internet as well. Only services you specify as allowed will be accessible over the internet. Apps like Plex require exceptions. You can find Firewall if you go to Control Panel – Security – Firewall
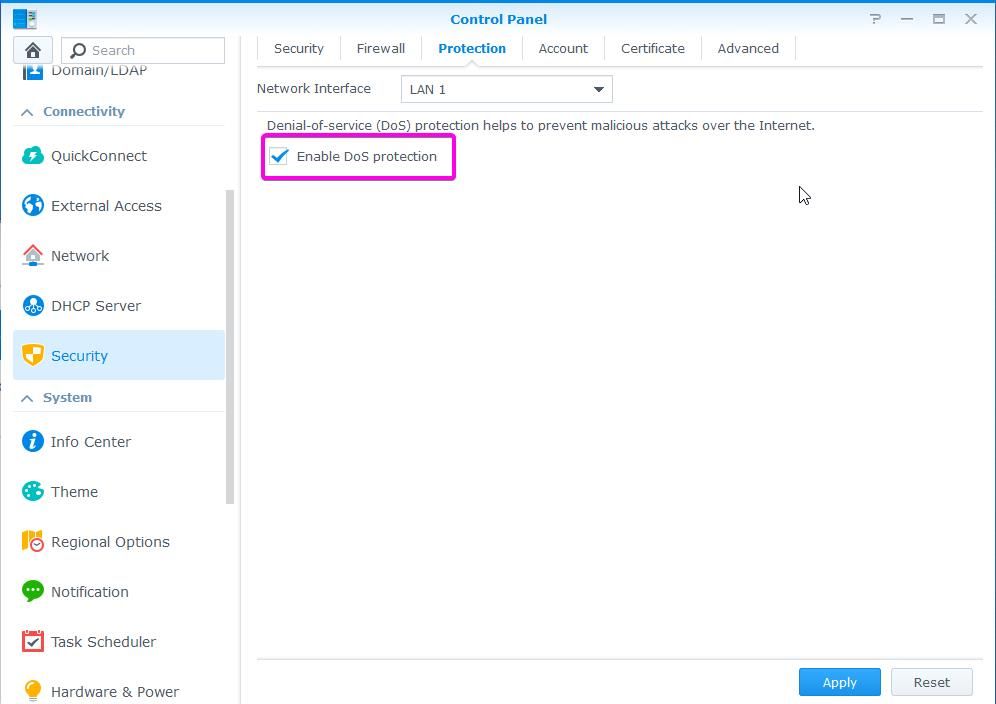
You can enable Denial-of-service (DoS) protection to prevent malicious attacks. Go to Security – Protection – Enable DoS protection.
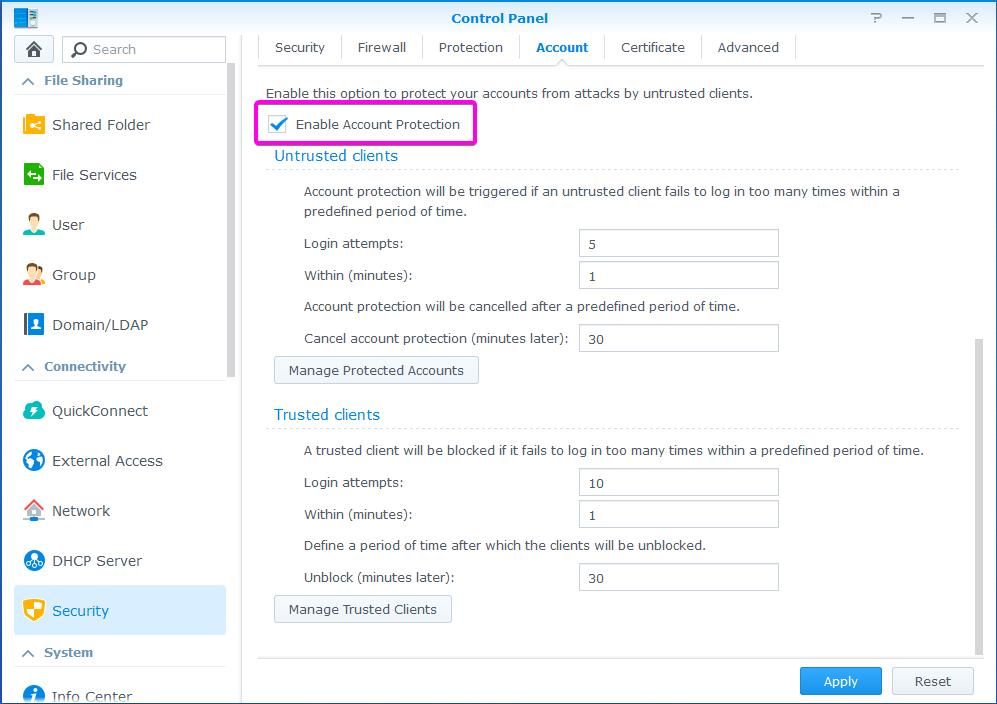
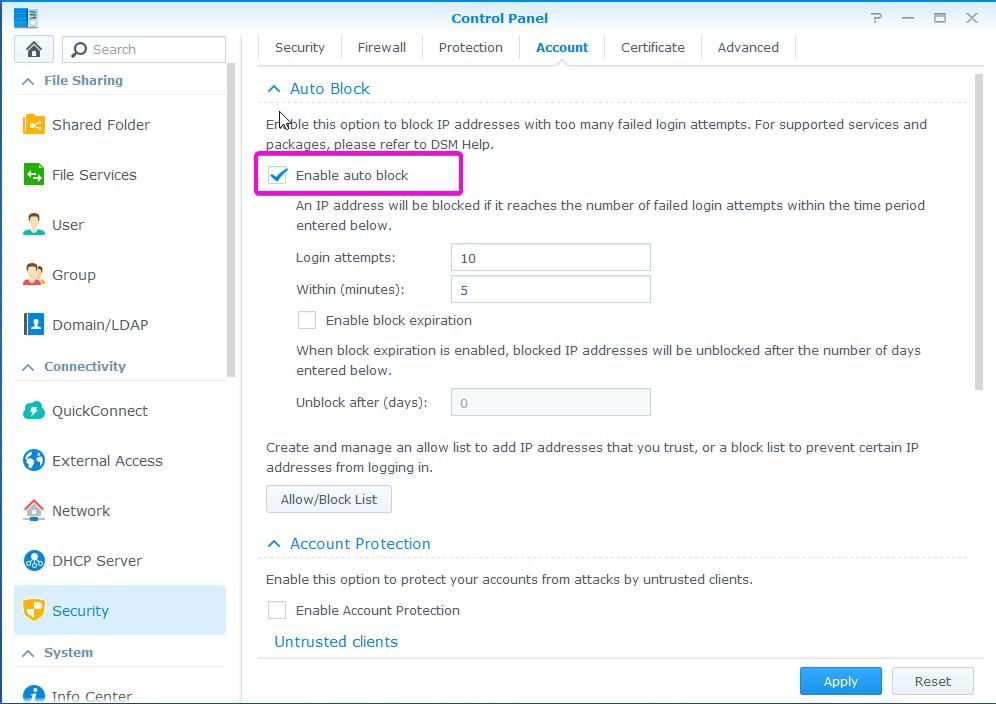
Enable Account Protection is a good and simple security feature. For example, if someone is trying to login to your NAS, and is trying to guess a username and a password, Synology DSM will block that person. Default parameters are solid, and you can increase account protection time. In the Control Panel got to Security – Account
Auto Block is similar to the Enable Account Protection feature. When you enable Auto Block, originating IP will be blocked. You can enable block expiration, for example, if you have like a lot of users and don’t always have time to unblock them. That way you will prevent brute force but still enable unblock of users that just forgot their passwords. Maybe you can enable block expiration from the start when users need to adjust to a new login form.
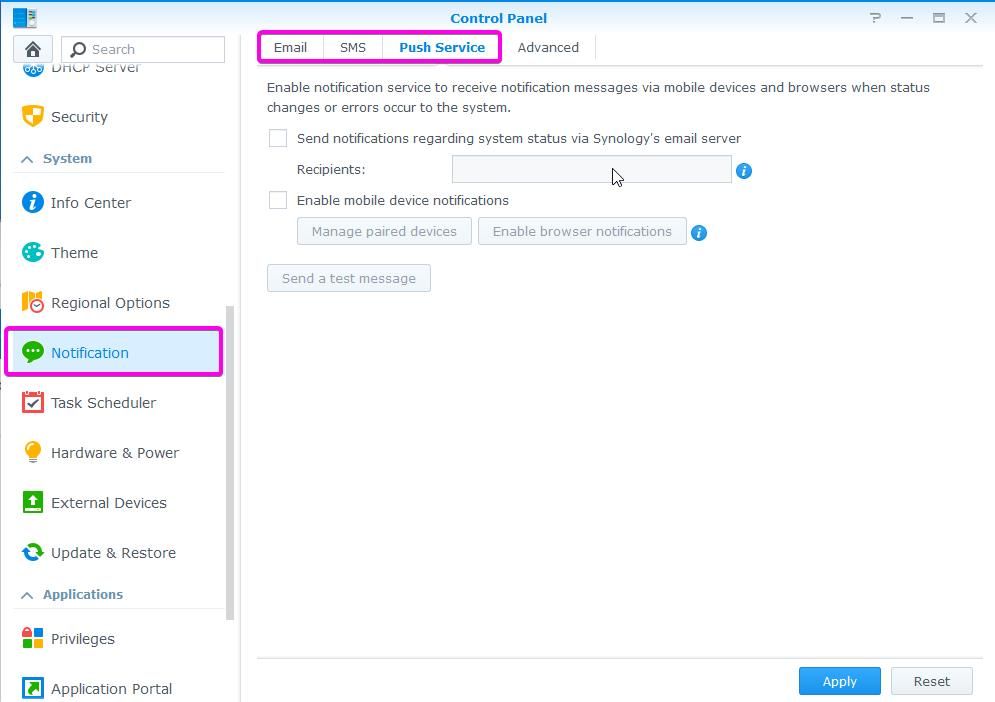
In Control Panel, Notification, you can enable notifications. You can choose from Email, SMS or Push Service. Notifications are recommended so that you get notified when special events occur. For example, when a hard drive fails, you may want to be notified so that you can replace it soon. You can also enable security notification for security events, like when the malware is detected, when Security Risks are found when DSM or applications are out of date, or when the system has detected a new login behavior.
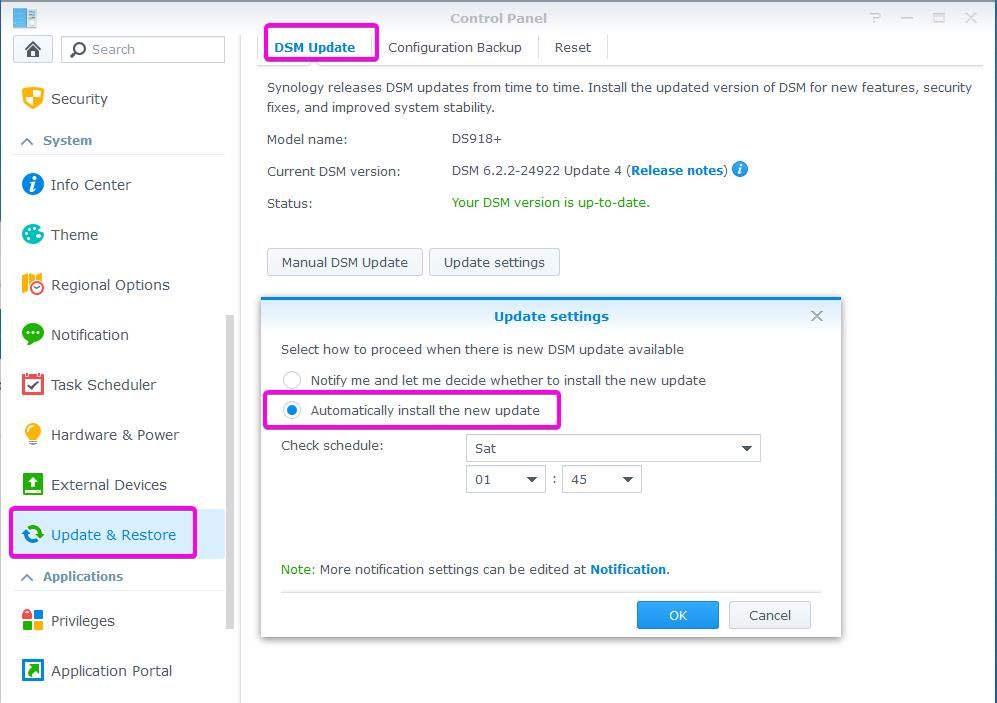
Every computer is running an operating system. For example, on a PC you can find MS Windows or Linux. On a MAC computer, you will find OSX. Operating System is constantly updated with new features and security updates. Synology NAS also uses an operating system called DSM that requires regular security updates. If you don’t update DSM, you may be running into a problem. There were cases when special malware was targeting NAS operating systems. If it found unpatched OS, it infected NAS with crypto locker virus. But if the NAS owner kept his/her NAS up to date, the infection could not spread to the NAS. You can enable the auto-update of the DSM operating system. You can set up a schedule so that the update happens when you are not watching movies for example.
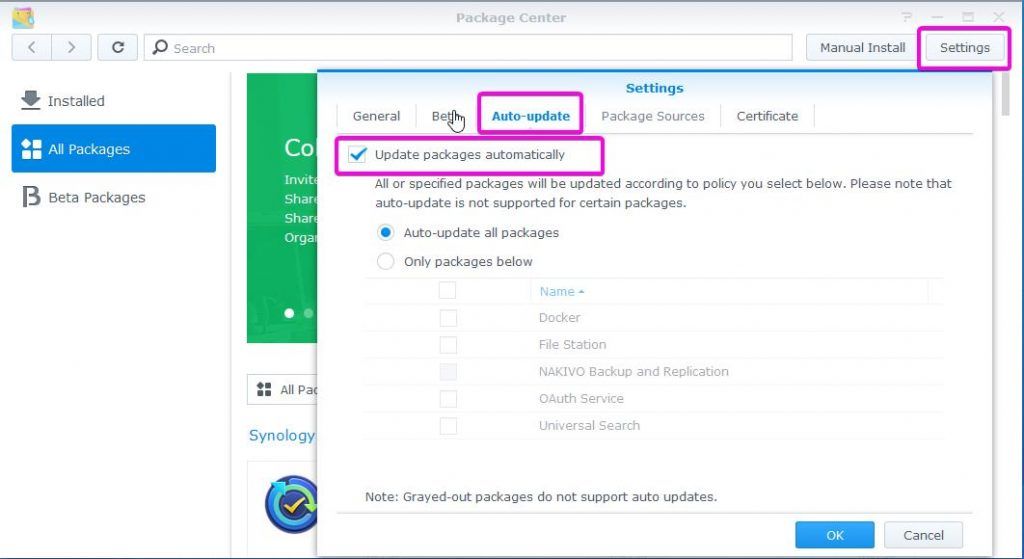
Just like the operation system, applications can be vulnerable to exploits as well. Regular updates keep the system clean. You can enable the auto-update of applications as well.
A reason why one of the first crypto locker viruses spread so quickly on the computer networks was the use of outdated SMB protocol on Microsoft Windows. Companies had to disable SMB1 on their networks and separate devices where that was not possible. For example, old operating systems Windows XP and Windows Server 2003 had to be moved from the rest of the network. By default, SMB1 is running on Synology for increased compatibility. You should disable SMB1 as soon as possible. In a corporate network, you really should not be using SMB1. If you disable SMB1 in-home network, you should test applications like media players. Some still have not updated to the SMB2. If that is the case, you can find other programs on the Play store or even better, you can send email to the author asking for the update.
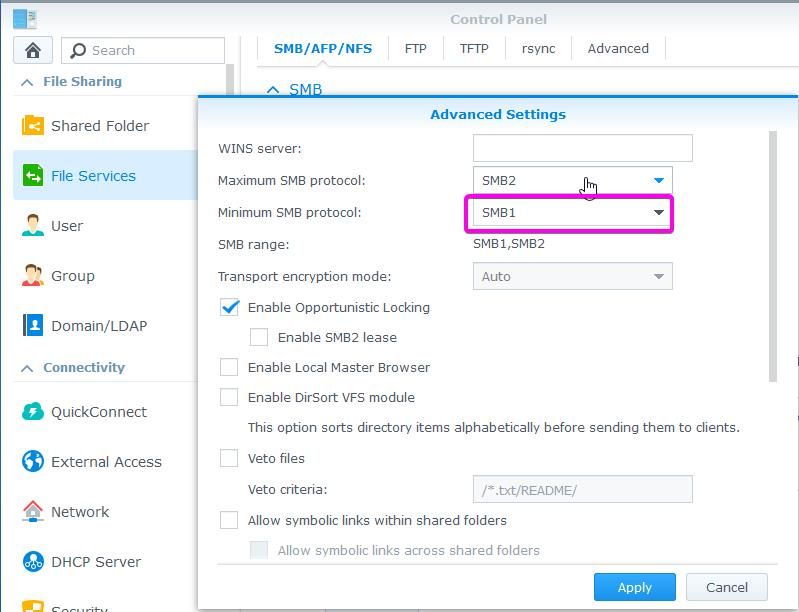
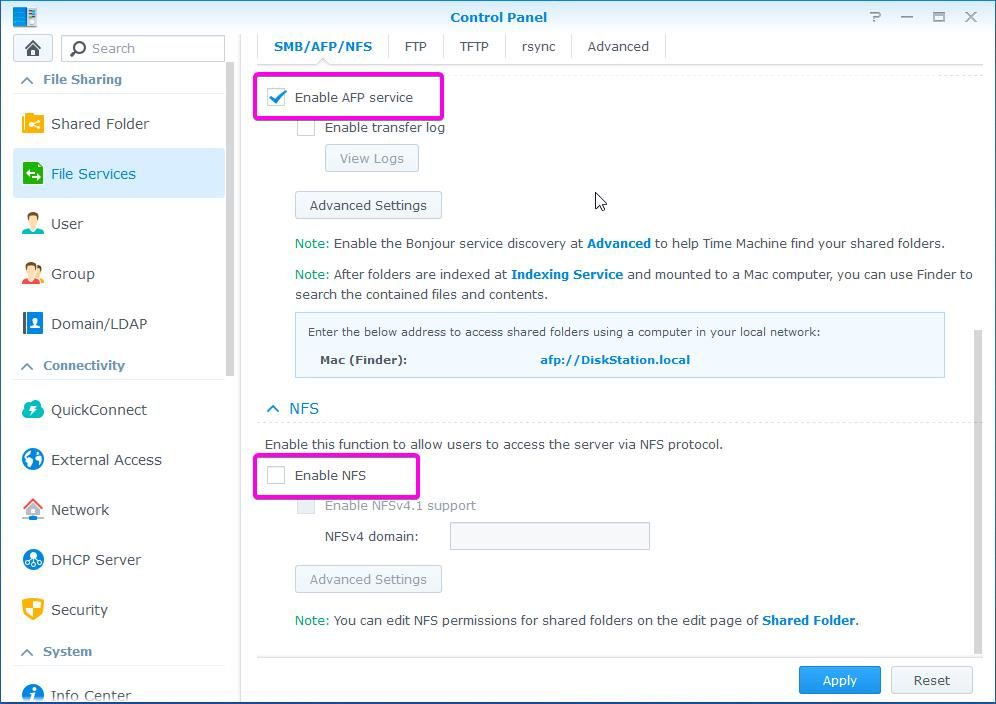
What protocols are really required on your network? Do you really need (do you use Apple MAC) AFP service? Do you use NFS? If not, you can disable both protocols.
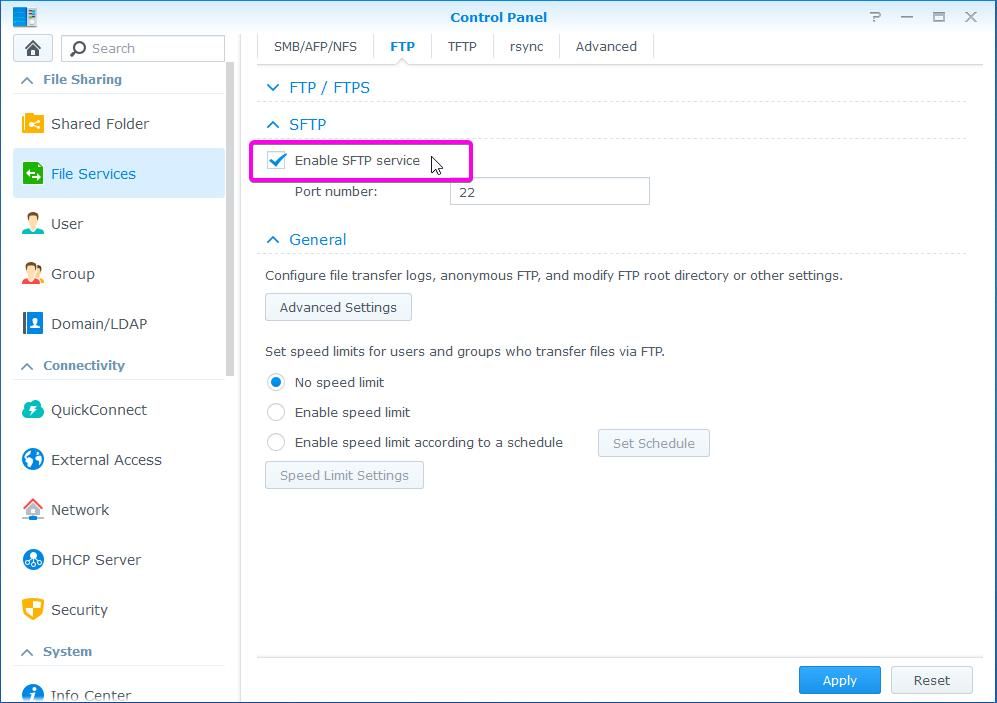
The same applies to FTP and SFTP. Do you need FTP? Perhaps it is better to switch to SFTP for increased security.
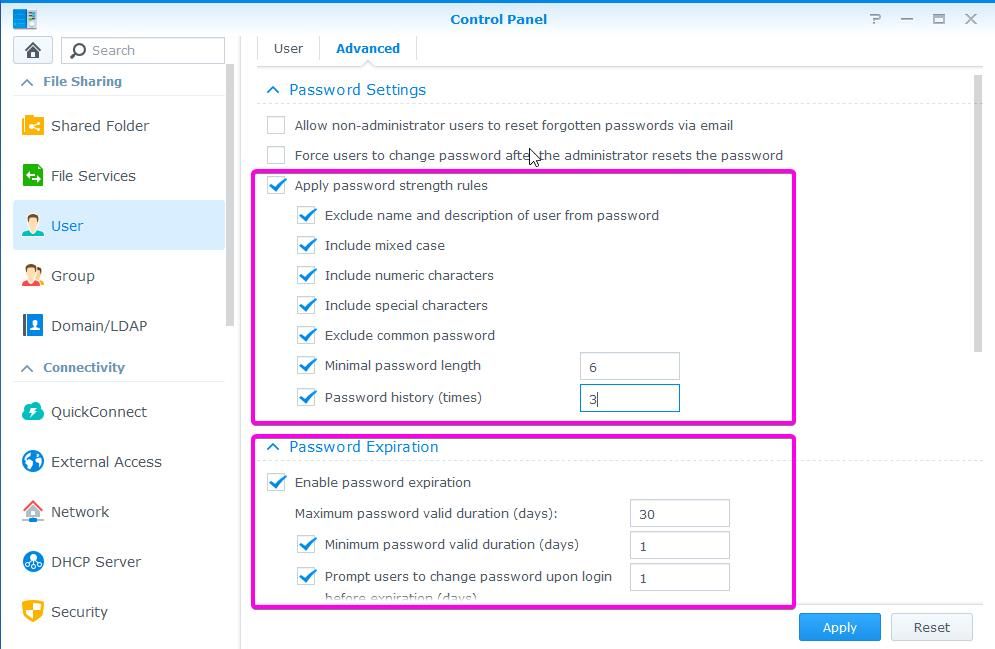
When you have multiple users on your NAS, for example, a company using NAS, you can enable complex passwords for increased security. You can also enable and tweak Password expiration.
Administrators of NAS systems should enable 2-step verification. If your password is compromised, the attacker would also need the second factor for authentication. Without the code, he or she can not proceed. When you have more that one admin for the NAS, you can enable that feature globally for all admins.
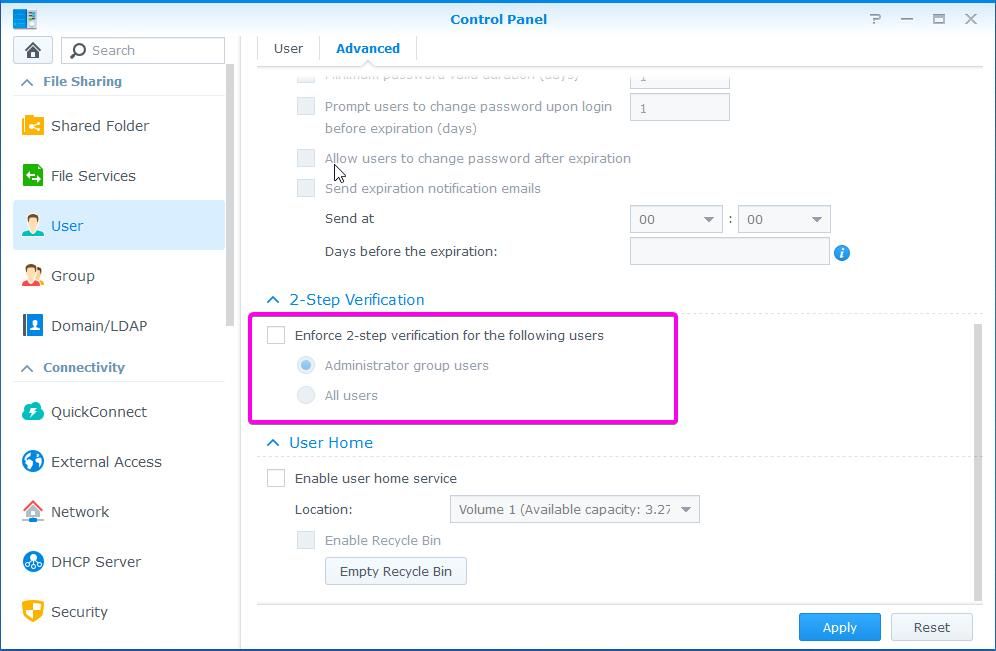
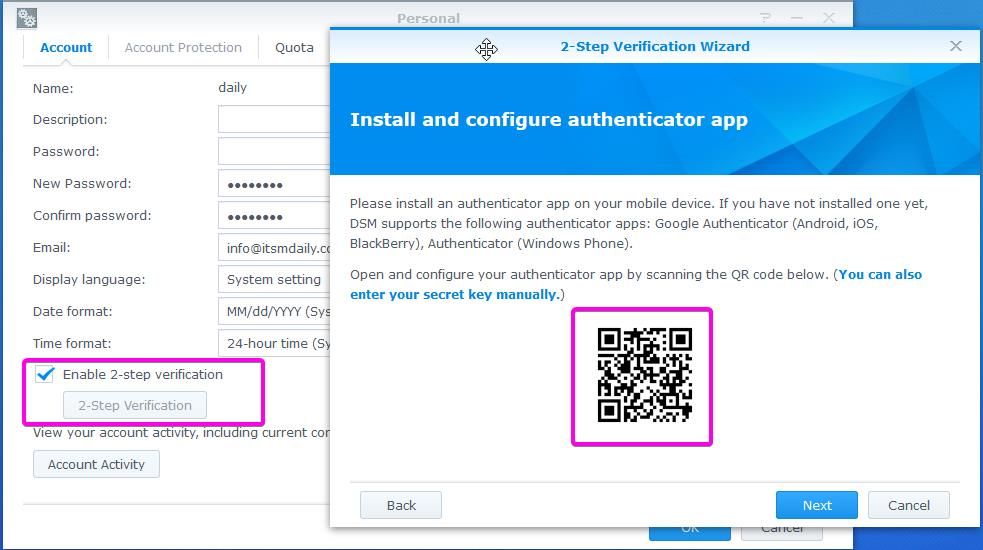
But if you are the only one who manages NAS, for example at home, you can just click on the top right corner on the person icon and select Personal. You will see the screen below. Click on Enable 2-step verification and follow the wizard. In the end, you can scan the code with applications like Google Authenticator on your phone.
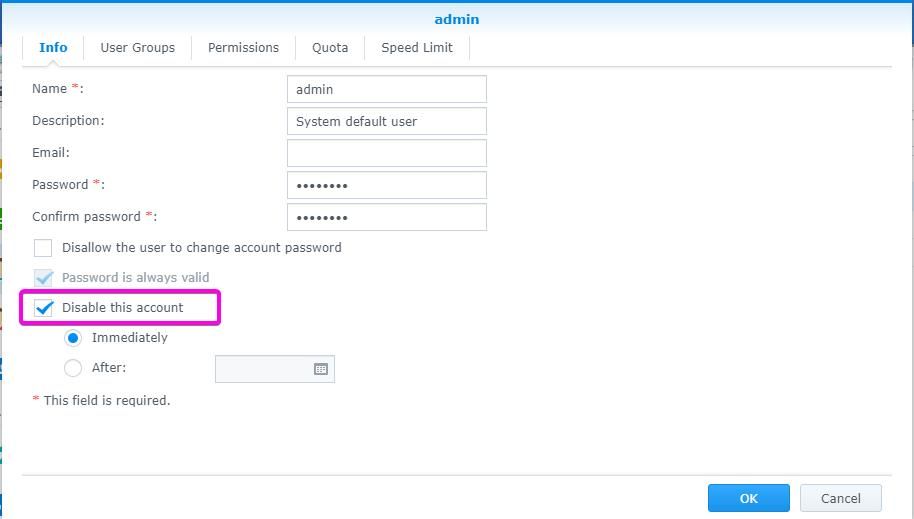
A good security practice is to create a new Administrator and disable built-in Admin.
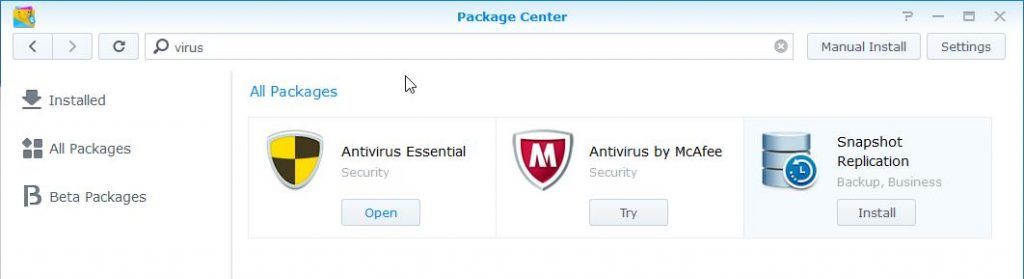
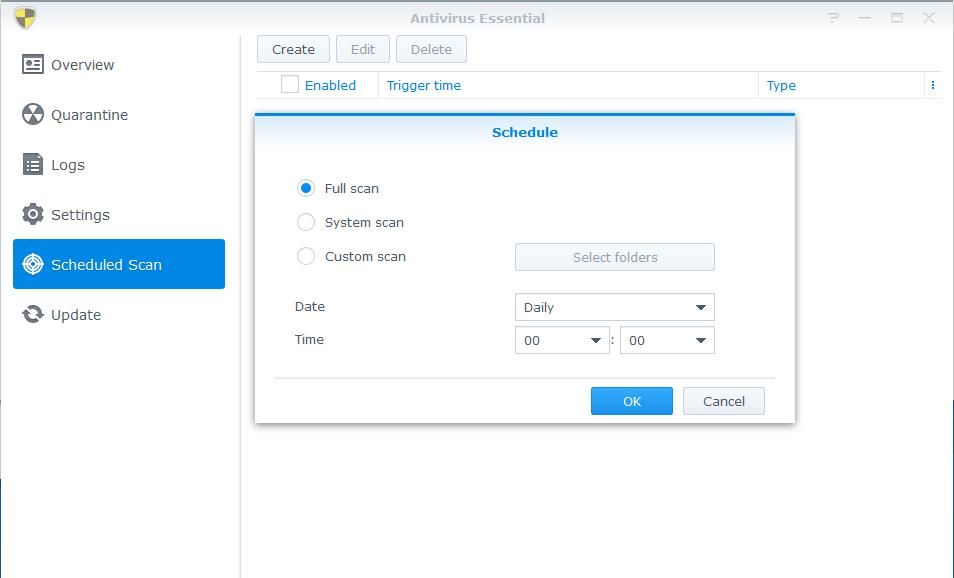
Anti Virus is an essential part of security protection. Antivirus essential is based on the open-source solution. It is not the best and it may miss a virus or two, especially if the virus is newer. But is free. I guess home use is better than nothing. For corporate environments, I would advise choosing Antivirus by McAfee. It is quite affordable. The only thing missing from both options is live protection.
You can enable a Schedule though. For example, you can start the on-demand scan based on the schedule you set. You can create multiple and can cover daily use. Also, you can adjust a Schedule based on the number of files you have.
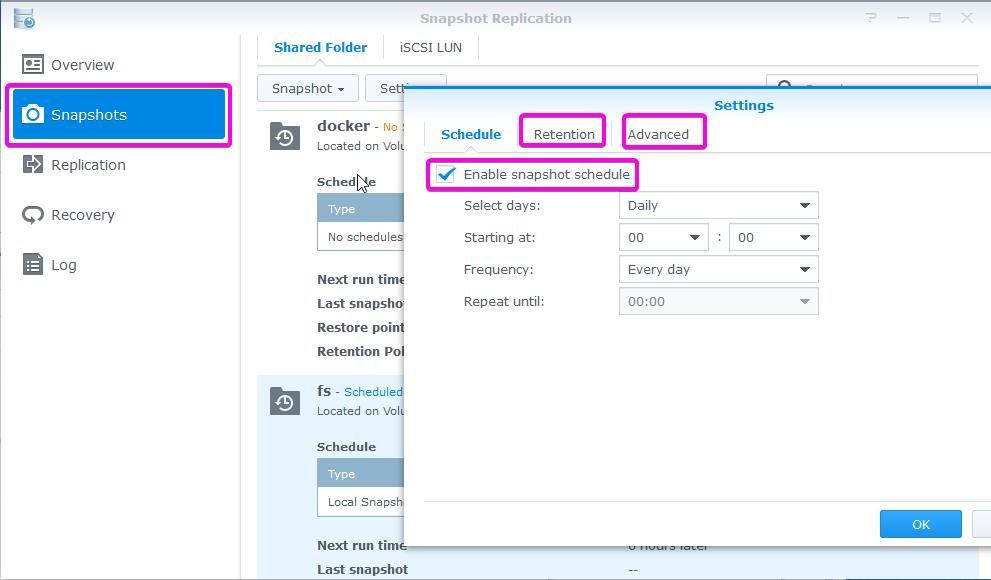
Are you using file shares? If you are, then you can’t prevent crypto lockers from encrypting files. In that case, the best protection is backup. There is no excuse to not backup Synology. You can install amazing backup programs. When Cryptolocker invaded a company where I worked, I solved the problem by using a shadow copy. When I found and removed the source of the problem, I restored all the files in a second. You can also enable a shadow copy type of functionality. But, your file system has to be BTRFS. Install Snapshot replication. Under snapshots, you enable the snapshot schedule. Under Advanced, you can select how many snapshots you want.
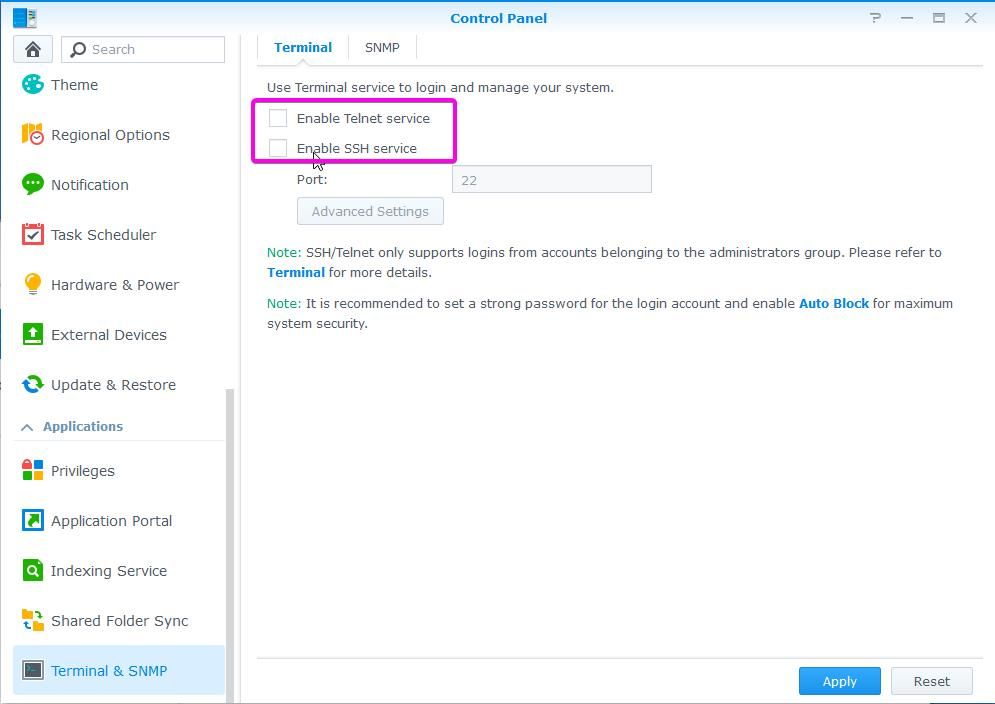
If you have been playing with Telnet or SSH, you should know that If those services are left enabled, they can be potentially used for bad things. Those two services are probably disabled, but just in case check they are not in use, especially if there are more than one admins.
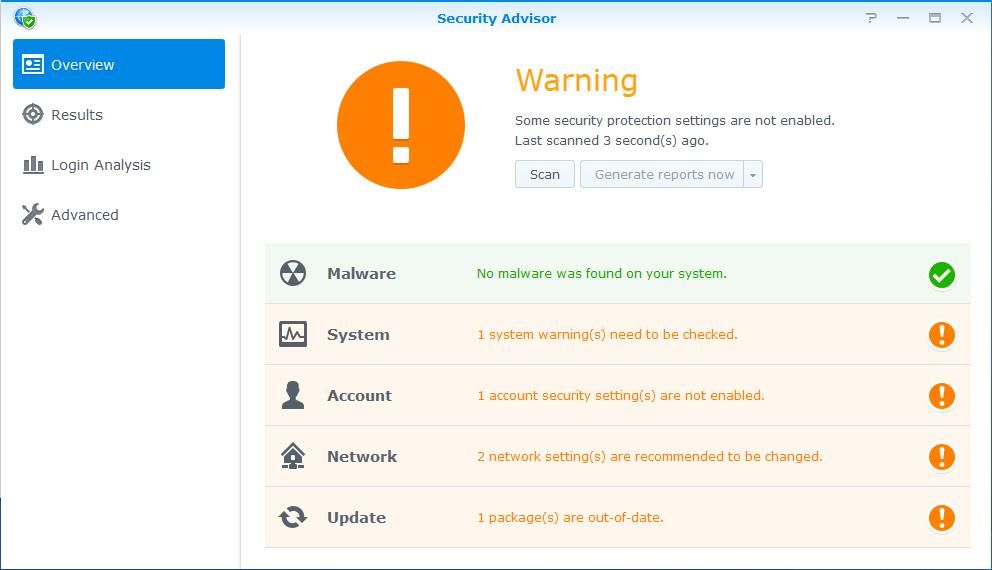
You should check the Security Advisor on a regular basis. It is a built-in security improvement system. It will scan for vulnerabilities and good practice security improvements. You can also schedule it and receive the result via email.
Data loss and ransomware encryption is a threat that can happen at any time. It is important that we are prepared for those times. A backup is an essential tool for when the worst happens. By securing your NAS, you can harden and even prevent the worst from happening.


Napsat komentář