Unified Endpoint Management (UEM) allows businesses to control and manage PCs along with smartphones and tablets by applying unified policies among them. Earlier, Mobile Device Management and PC management were two different ideas and existed as two products. With Unified Endpoint Management, users benefit from using a single product for managing mobile devices and PCs.
Why UEM?
With the introduction of Windows 10, industries started moving towards to the idea of managing PCs along with their mobile devices. This includes applying all configurations and restrictions available for mobile devices, along with PC-specific restrictions like blocking a device connected to the USB ports.
There is a significant demand for PC management and Mobile Device Management, so uniting them will be a good idea. Although there’s news that most of the industries are switching to mobile computing, eliminating the requirement for a PC management solution, more number of Macs are sold this year than the previous, which prove that the PC management options will be active in UEM and get constant updates.
UEM vs MDM vs EMM
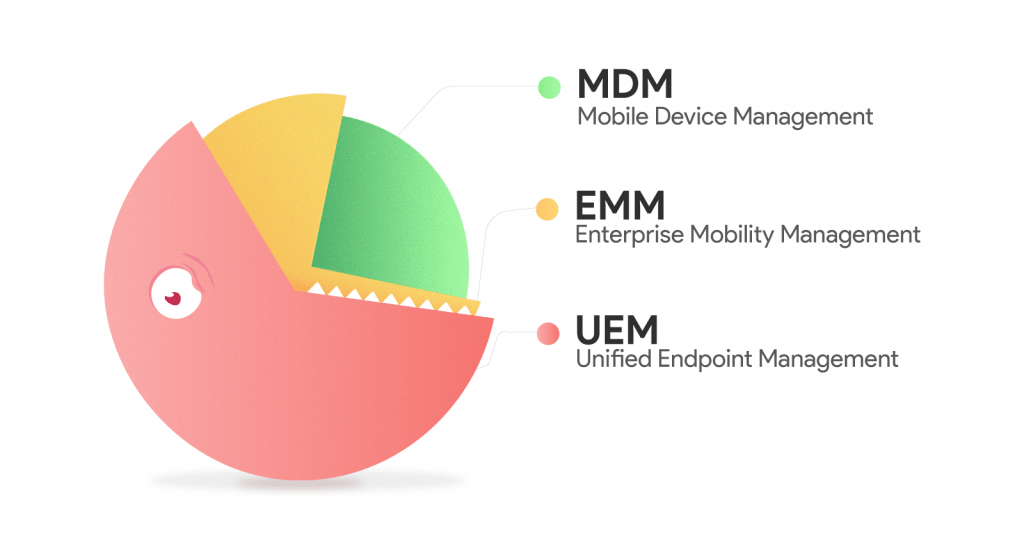
The illustration says it, but a few. So, let us explain:
Mobile Device Management (MDM) is the provisioning and management of mobile devices the employee owns or the one given to the employee, primarily to secure corporate data in it. Mostly based on BYOD (Bring Your Own Device) strategy, MDM contains a lot of restriction and configuration options to manage mobile devices, supporting Android, iOS and Windows mobile devices, with some vendors supporting BlackBerry and Symbian as well.
The concept of Enterprise Mobility Management (EMM) is vast and is not limited to managing restrictions, it provides other options like content management, application management and security features like containerization and protection from security attacks, to name a few.
With Unified Endpoint Management, device management expands from mobile devices to desktops (Windows and Mac) and wearables, and even began supporting Internet of Things devices. Compared to MDM and EMM, UEM possesses more capabilities as desktops have a lot of features than the mobile devices to be restricted, and Windows is more vulnerable to virus attacks, with the recent attack to the new „secure“ Windows 10 S release. App installation prevention feature in Windows requires blocking installation of Windows Store apps (appx), desktops apps (exe) and Windows installers aka Microsoft installers (msi).
Hexnode MDM and endpoint management
Hexnode MDM, a familiar name in Mobile Device Management has expanded their portfolio to include UEM as well. The features include password, device and iCloud restrictions, network configuration, location tracking and device wipe for laptops and desktops, along with the mobile device management features.
Password restrictions can be set up with the desired complexity requirements to improve security by preventing unauthorized access. Device restrictions like camera usage, music access, auto-unlock, AirPrint, copy-paste, voice recording, USB connection etc., are an added advantage. IT administrators gain more control over the employees and their actions and secure the data from moving out. In Macs, iCloud services like Back to My Mac, Find My Mac, Find My iPhone, mail, calendar, address book, reminder notes and data sync can be allowed or disallowed.
WiFi, VPN, Email, ActiveSync and LDAP can be set up remotely and pushed to the device over-the-air which saves time in setting up these in every system/platform. Although location tracking is of minor use for desktops, laptops and other mobile devices can be tracked down to know where the device or the employee is. Geofencing can be used to set up location-specific policies for individual devices or device groups. With Content Management, send files to a specific location on the device, have them saved without confirmation from the user and let them open and view them right within the Hexnode MDM app.
As a security add-on, if the device is lost or stolen, device wipe feature wipes the whole data off the device and resets it to prevent the corporate data from being compromised. Integrated app and kiosk management options make it easy to distribute and deploy apps in bulk and set kiosks with additional device management capabilities. Remote view and control help to view and interact with the device screen remotely, which reduces the effort of troubleshooting.


Schreibe einen Kommentar